‹ Back to all stories
Ardit Berisha: Building Amaro Than Like a Fortress, One Line of Code at a Time
Amaro Than Team · Nov 23, 2025
Ardit Berisha designed Amaro Than like a system under constant, invisible attack. As a cyber securist, he starts every diagram from the attacker’s view: where to slip in, where to exfiltrate, where to break trust. He doesn’t just draw boxes and arrows; he maps entry points, blast radius, and fail-safes, then asks, “What happens if this fails—and who notices first?”
From the first server boot, security is treated as a living organism, not a feature bolted on at the end. The backbone runs across multiple servers with Nginx and Apache, carefully segmented so no single breach exposes everything. Frontend, APIs, databases, background workers, and media processing live in their own zones. If one layer is hit, the others don’t fall with it.
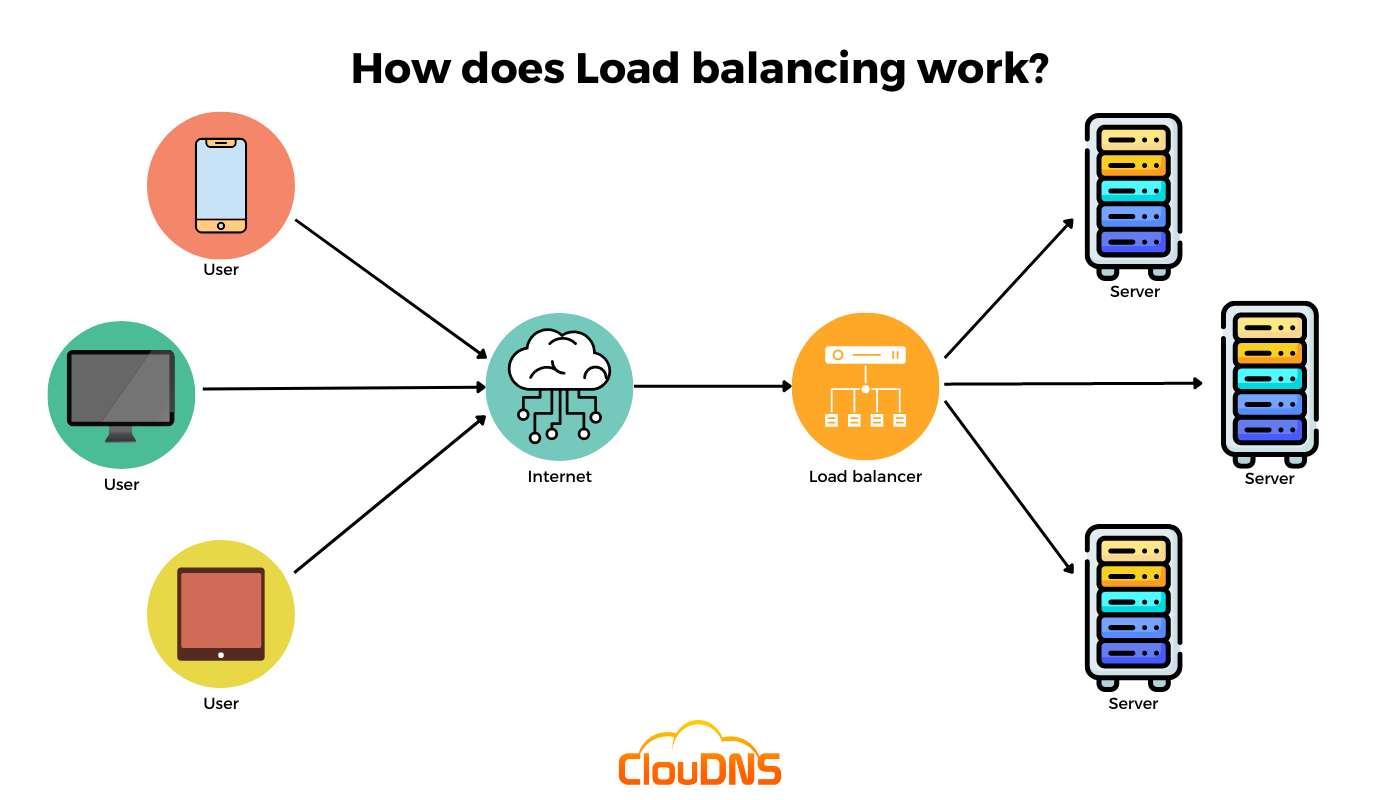
Every layer is designed to stay scalable and secure at the same time. Load balancers sit at the edge, routing traffic to clusters of application servers that can grow horizontally. When usage spikes—new users, viral posts, heavy video uploads—the system doesn’t panic. It scales out: new nodes come online, caches warm up, and queues stretch instead of snapping. Scalability is not an afterthought; it’s baked into every decision Ardit makes.
Traffic flows through strict rate-limits, WAF rules, and layered auth. Every request is tagged, logged, and scored in real time. Custom algorithms watch network activity, learning what “normal” looks like so they can flag DDoS waves, brute-force storms, or credential-stuffing bursts the instant they begin. When abnormal patterns appear, automatic rules can slow them down, challenge them, or drop them completely—without slowing real users.
Behind the scenes, honeypots quietly pretend to be weak spots: fake admin panels, fake APIs, fake databases that no normal user would ever touch. Hackers are drawn into these decoys, revealing their tools and behavior, while the real systems stay locked away. Every hit on a honeypot is not just blocked—it’s logged, analyzed, and turned into a defense lesson for the future.
The data layer is designed for both safety and growth. Databases are split and isolated by purpose: users, posts, analytics, moderation, logs. As traffic grows, these databases can be sharded, replicated, and distributed across multiple machines and regions. But no direct query ever touches raw data without strict validation and prepared statements. SQL injection payloads are filtered, recorded, and converted into signatures that help strengthen new protections. Every failed attack attempt becomes training material.
CSRF protections wrap every action that matters. Tokens rotate. Sessions are scoped carefully to devices and actions. Origin checks and same-site rules make sure that clicks and API calls truly belong to the user who made them. Passwords are never stored in plain text, only as strong hashes with modern algorithms and proper salting. Sensitive actions—changing email, deleting accounts, managing payments—demand extra verification, not blind trust in a single cookie or token.
Encryption is non-negotiable. Every critical field flows through AES-256-CBC, from personal data to private messages. The master key is not a static secret lost in a config file; it lives in a secure vault and rotates on a strict schedule. Each week, background processes re-encrypt stored data with a fresh key, while the old one is retired and safely destroyed. Even if someone somehow stole a database snapshot, it would quickly decay into useless noise. The system assumes compromise and still aims to be safe.
Alert systems run like a heartbeat, 24/7. If something spikes—login failures, strange IP clusters, unusual read/write patterns, abnormal latency—Amaro Than raises alarms automatically. Dashboards light up. Notifications ping the team. Automated playbooks can throttle traffic, activate stricter firewall rules, move certain services into isolation, or force additional verification for at-risk accounts. Human engineers step in with context, but the first response is always automatic and fast.
Scalability is always paired with observability. Logs, metrics, and traces are collected from every part of the stack. Ardit designs the system so that every request leaves a breadcrumb trail: which service handled it, how long it took, what database it touched. When the user base grows from thousands to millions, this visibility doesn’t vanish—it becomes the reason the system can keep growing without collapsing under its own complexity.
Media—images, videos, audio—is handled just as carefully. Upload endpoints enforce strict limits, content validation, and type checking. Media is offloaded to specialized storage and streamed efficiently, so application servers don’t suffocate under bandwidth. Queue workers process heavy tasks asynchronously, keeping the main experience fast. Even in this media pipeline, Ardit thinks like an attacker: what if someone tries to upload malicious files, oversized payloads, or crafted formats? Filters, scanners, and sandboxed processing provide the answer.
APIs are versioned and locked behind authentication and permission checks. There is no “open door” endpoint; everything is designed with the assumption that someone, somewhere, will try to script it, abuse it, or reverse-engineer it. Rate-limits by user, IP, and token help prevent abuse. Abuse patterns—like mass account creation, follow/unfollow spam, or automated posting—are recognized by behavioral models, not just simple counters.
Underneath all of this, Ardit keeps one principle: the system must be able to grow without becoming fragile. That means decoupling services, building clear boundaries between components, and designing for failure. Nodes can go down without users noticing. Databases can fail over. Caches can be rebuilt. The architecture is designed so that individual parts can be replaced or upgraded while the platform keeps breathing.
For every new feature—stories, chat, notifications, profiles, discovery—there is a ritual. The team designs what users will see, and Ardit designs how attackers might abuse it. Only when those attack paths are mapped, mitigated, and tested does the feature move forward. Security is not a separate checklist at the end; it walks with the feature from the first sketch.
In the end, the architecture of Amaro Than is more than servers, nodes, and keys. It is a promise that Roma communities can connect inside a platform built by someone who thinks like a hacker, architects like an engineer, and guards like a defender. Every packet, every query, every replica, every shard is designed with the same rule in mind:
Security comes first, and scalability is built to protect it—not weaken it.
 Featured
Featured